

Only the admin of your instance can see your IP address, it doesn’t get federated to other instances.


Only the admin of your instance can see your IP address, it doesn’t get federated to other instances.


Thanks for the analogy, that really helps to put it in perspective. I was trying to work out the number of molecules per metre that would leave you with, but either my sense of scales is off kilter or I’ve got it wrong.
From what I can find, there are approximately 2.5e25 molecules per m3 at 1atm. Given an 11km cube has a volume of 1.3e12 m3, that gives around 2e13 molecules per m3 per m3 released. That sounds high, have I got the figures wrong somewhere?


It tracks the location of a body (or anything else that causes the same sort if interference), but it doesn’t identify the person, and as such they can reasonably make the claim that this technology is privacy preserving.
Of course, as with anything that claims to anonymise data, or preserve privacy, that assertion starts to fall down when you use the resulting data in conjunction with other data sources, even if they too claim to be privacy preserving.
That’s pretty much what a mercury thermometer does. As the temperature changes so does the volume of the mercury, which causes the level to move up and down, and the temperature scale on the side is just a measure of how high the mercury reaches.


I don’t think it’s abuse they love exectly, it’s being told exactly what to think and how to act. It removes a huge amount of cognative load and uncertainty and leaves them feeling more sure of themselves.
It’s been quite a while since I’ve used sleep on a laptop, but it worked well on my Dell (latitude I think, as I said, it’s been a while). It did take a little experimenting with sleep levels to get it reliable, but once it was it worked for years.
ETA: I realise that saying “it worked for me” is probably intensely annoying, my appologies for that, but I thought a counterpoint might be a useful extra data point.


Destroying the encryption key tends to be the only reliable way to put the data beyond use. Physical destruction techniques like the obe in the article have been tried before, and iften leave the data intact, just destroying the driver side of the chips. It’s not easy to retrieve the data, but a sufficiently determined and resourced oppinent can do it.
Obviously, there’s no reason not to do both, for added certainty, but if the encryption protocols used in proper FDE are compromised, we have a lot more to worry about.


It does seem like it would be simpler and more reliable to use full disk encryption to encrypt the data before it’s written, and just destroy the key if you want to nuke the data.


It’s a bit ambiguous, so you could be right, but I took it to mean that activation of the receptors was that active mechanism, regardless of cause. Psilicin is just the compound they’re focused on, and maybe it does activate them in some unique way that has this effect, but the summary didn’t make that clear.
If there are alternative pathways to activate the receptors they may be better suited to thereputic use without the psycadelic side effects.


I haven’t gone looking forthe souce paper, but from the article it looks like seretonin was the actual compound that’s having a beneficial effect, specifically serotonin outside the brain.

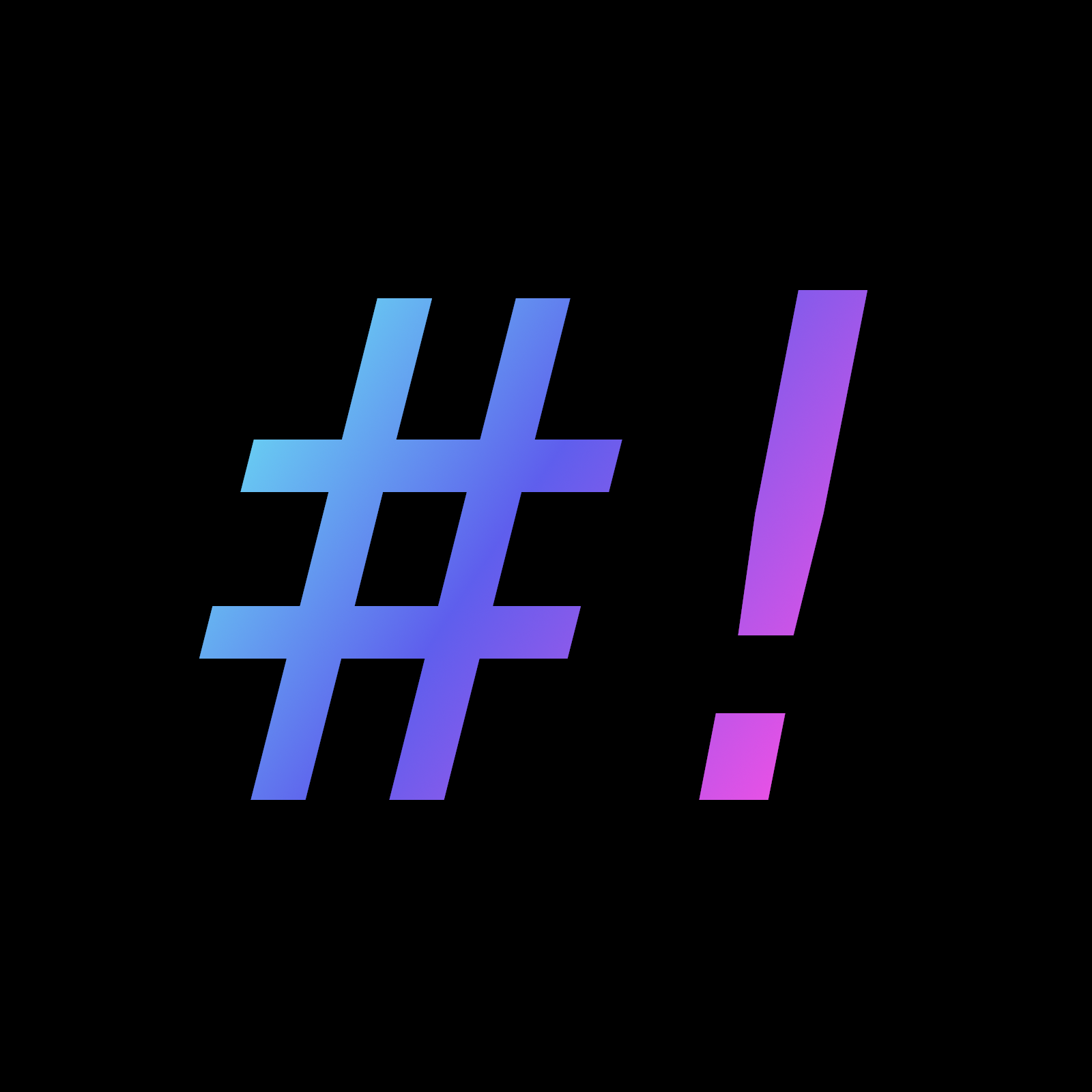
The bash man page is full of useful bits like this, but is is densely packed. It’s definitely worth reading though.

You can use the <( ) replacement for this as it runs a command in a subshell and replaces it with the filename of a temporary fifo. So something like:
join <( echo "${var1}" ) <( echo "${var2}" )


I assume it’s been vibe coded, sauce for the goose being good with the gander and all that.
ETA: /s just to be clear.
Fair, that maybe came across harsher than I meant. Refusing to provide packages because you don’t use the system is fine, but please provide a tarball that I can unpack, rather than some dodgy script that has to try to work with the differences in those ststems anyway.
Better to do away with the entire concept of downloading and running a shell script like that, and use distro native packages instead. It’s not hard to create DEB or RPM packages, ebuilds aren’t too bad either, and it sounds like AUR packages are managable too.
The entire concept of blindly downloading a script, running it as root, and hoping that, in the best case, it’d install the version of the software you want is a bit crazy. If the upstream developers refuse to provide packages, please, at least, provide a tarball.


While there’s probably no global solution, personally I use a QR Code reader that doesn’t actually use the URL, but just displays it and lets me copy it to the clipboard. That way I can inspect it, and if it doesn’t look right, ignore it.


This is excellent article on enshitification, some of the factors that can lead to it, and ways founders could think about it to hopefully avoid it. What it doesn’t seem to talk about is how Tailscale intends to avoid it, now and in the future.
The joys of distributed algorithms. You can now get more errors, more quickly than before!
I remember writing a chat system in assembler, for DOS, using, IIRC, IPX networking. When it went wrong, one or more machines would just freeze, with the string “NETWORK ABEND” in the middle of the screen.
I should fork vim and call it ‘death’, so I can shout “give me vim or give me death!” any time someone suggests a different editor.
Oh, you should absolutely go there again, as should many other people, but only to explain to the manager, in detail, exactly how unacceptable this is, and to demand proof that they have written policies forbidding their staff from engaging in this sort of behaviour. Then contact law enforcement to ush them to prosecute to the maximum extent possible.